On June 19, menshn.com launched giving me a couple of days to have a look around, but not enough time to write up any serious thoughts before going on vacation. The site launched only in the US and visitors from the UK and elsewhere were greeted with a holding page. However, like many technically aware individuals, geographic barriers are no match to those with VPNs, VPSes or just a simple web proxy.
Initially, only three “topics” were available, a (US) Election2012 topic and one each for Obama and Romney.
Menshn has taken a bit of a battering on Twitter over, I guess, pretty much every aspect of the site imaginable.
Some don’t like the owners, one UK Conservative Member of Parliament, Louise Mensch, and a former Labour advisor Luke Bozier. However, the primary focus of much of the complaints are the web site’s numerous and shocking security flaws.
I believe I was one of the first (if not the first) to highlight the Cross Site Scripting Security flaws. Though I did not actively demonstrate (exploit) it having previously burned in this area, others such as James Coglan have demonstrated the complete lack of data validation that abounds on Menshn.
The site launched without using a SSL Certificate allowing passwords to pass in plain text – a flaw I missed – but ably spotted by Suggy and Andrew White.
Also prior to going on vacation I highlighted two examples of Copyright Infringement to both Louise and Luke. The first was the alleged unauthorised use of the Obama HOPE poster which I screen captured here:
I was completely ignored.
Then Menshn created a new topic “Women” for which they used another image of a “thoughtful woman”:
Note – screen cap of Menshn is on left; the same image I found on Elite Dating Agency site (using Google image search, honest!). I tweeted to Luke, who responded that the image was Creative Commons. However, this I doubted as I can generally spot a professional image and eventually found the real source as a Premium Stock Image that they could have paid just $9.99 to use. The image soon disappeared from Menshn without further comment from Menshn.
Edit: Just found another image on Menshn – the image for the UKPolitics topic – that does not adhere to the Copyright owner’s license:
The original image is owned by Kevin Shakespeare with the license of “Attribution, Non-Commercial, and No Derivative Works”. Another Menshn fail.
I like to think I’ve educated them a little on Copyright law.
And finally, the straw that breaks the camels back.
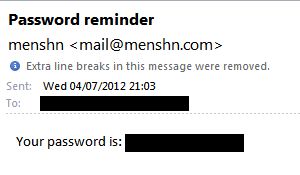
Back from vacation, try to login, but of course I forgot the password and so used the “forgot my password”. Now all normal security conscious web sites will create an encrypted, time limited, one-time use token or URL that you can use to reset your password and email that to you.
No, not Menshn. Menshn will email your actual password in plain text.
The horror. Not only does this mean your password flying through the world’s email servers (making it available to all sorts of Government interception) it also means that Menshn is storing your password inside its database using at best a two-way reversible encryption, or at worst in plain text.
Either way – it is a security disaster, A breach of the web site means all users and all passwords are exposed in plain text (with the reversal key available from the forgot password code). Luke should read http://www.phptherightway.com/#password_hashing_with_bcrypt .
An awesome coder he is not.
Post publication edit: This article has been mentioned in Business Insider –
We Speak To The British Politician Behind The Controversial 180-Character ‘Twitter-Killer’ Menshn




Ooops! SHA2 is SF?